Grokking the M2M Attack Matrices
Feb 10, 2024 23:10:33 GMT -6
Finarvyn, kipper, and 5 more like this
Post by waysoftheearth on Feb 10, 2024 23:10:33 GMT -6
Making sense of Chainmail's 2d6 Man-to-Man, Individual Missile Fire, and Fantasy Combat Tables can be something of an obsession. Particularly if you want to try out OD&D's implicit/default (i.e., non-Alternative) combat matrices.
To that end, I've spent an unjustifiable amount of time/effort in this area, and it has long been on my mind to share some of the outputs here before it all vanishes into oblivion.
Here, I present the Man-to-Man matrix with color (oo!) and percentages (oooh!), and then compare selected columns side-by-side in a hazy attempt to show what's going on. Hopefully, some of this might be useful to anyone interested in the crunch of it...
Man to Man (and Individual Missile Fire) Tables with Color
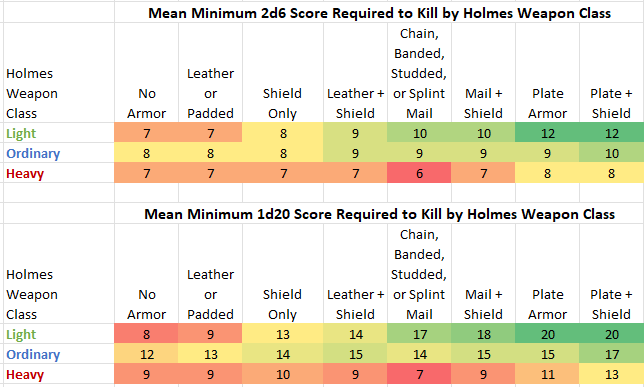
First up, let's take a look at the minimum (2d6) scores needed to kill (almost*) exactly as they appear in Chainmail, only with COLOR!
* I say "almost" because I have converted the handful of "/ = inability to kill" entries for medium and long range missile fire to 13s and 14s. This nominally means that positive adjustments due to high dexterity and/or magic bows or arrows make it possible to kill in a D&D context where it was impossible in a purely M2M context. Ignore these entries if you prefer.
TABLE #1
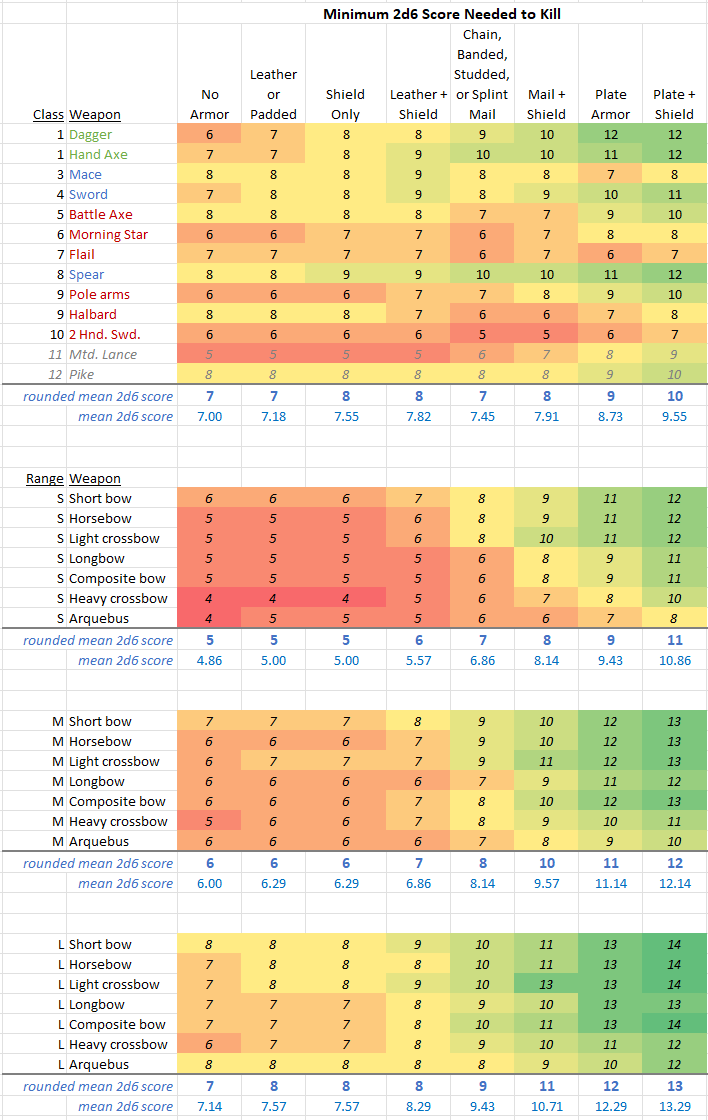
The color makes it clearer how effective each weapon type is versus each armor type. The redder a cell is, the more likely a kill. The greener a cell is, the less likely a kill.
Note also:
1. I've colored the melee weapons accorded to Holmes' classification of light (green), regular (blue), and heavy two-handed (red) weapons.
2. Below each weapon section, I've added (in blue) the rounded mean 2d6 score, and decimal 2d6 score required to kill versus each armor type. Mtd. Lance and Pike are excluded from these average calculations as these weapons don't occur in the dungeon exploration context.
Observations:
- The missile weapons show a neat kill probability progression, with both weapon types and armor types listed in least to most effective order. Short range is more effective that medium range, which is more effective than long range.
- The melee weapons do not show the same neat kill probability progression, despite the armor types still being listed in least to most effective order and weapons being listed in size/reach order.
- Considering the mean 2d6 scores required to kill in melee combat, armor other than plate/plate+ shield has small impact on survivorship.
- Considering the mean 2d6 scores required to kill with missile fire; missile fire is even more deadly than melee combat, and especially so for lightly or unarmored targets at short range.
How Effective is my Armor?
If we wanted to see more clearly how effective each ARMOR TYPE is compared to the last, we can simply put the appropriate pairs of columns together, like this:
TABLE #2
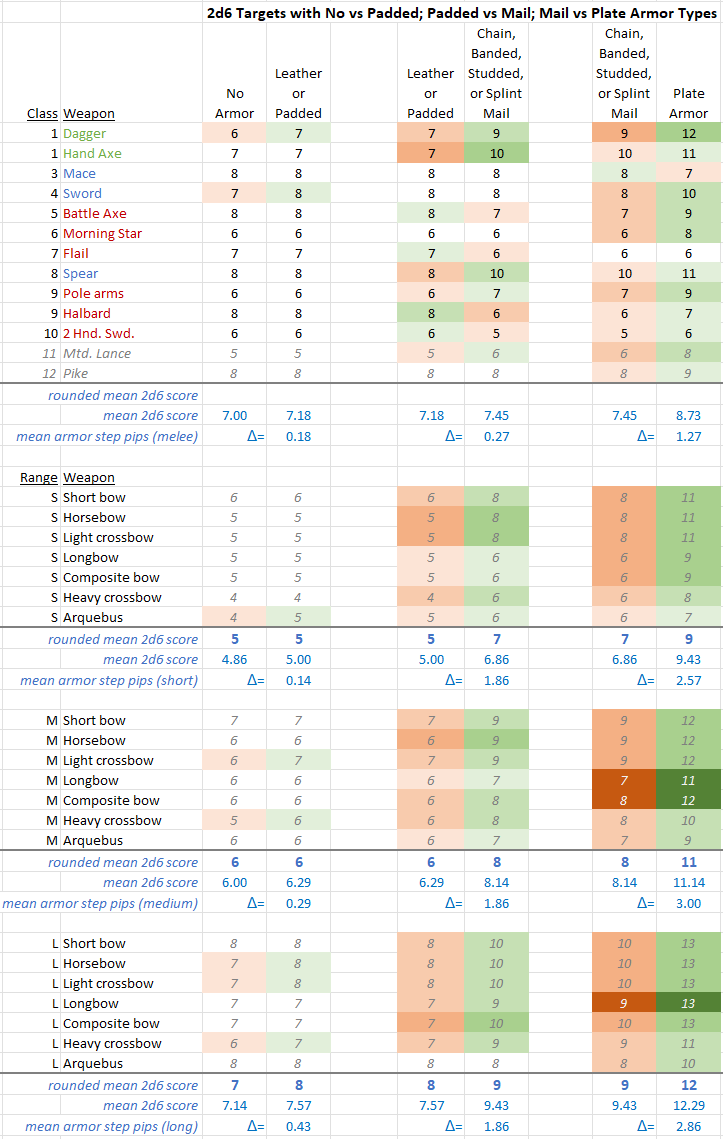
The color in this table indicates which armor, in each pair, offers better protection. Green is better protection, red is worse protection. No color indicates that protection is the same.
Below each section (in blue) I've again added the mean decimal 2d6 score required to kill versus each armor type (excluding Mtd. Lance and Pike). Below that, I've added the difference between each pair of means (the triangle, or delta, symbol) as a number of 2d6 pips.
Observations:
- Leather/padded armor is little better than no armor at all (expecting, perhaps, versus missiles at long range).
- Against melee weapons: mail armor (and its variants) is WORSE than leather/padded armor almost as often as it is better. In each case where mail is worse than leather/padded it is also worse than no armor at all!
- Against melee weapons: the improvement offered by plate amor is four-fold as great as the improvements offered by mail over padded/leather, or padded/leather over no armor at all.
- Against missile weapons: the improvement offered by plate amor is again almost double the improvements offered by mail over padded/leather, or padded/leather over no armor at all.
How Effective is my Shield?
Equally, we may wonder what protection SHIELDS offer on the M2M matrix. We can visualise this similarly by comparing the protection of each armor type without and then with shield, side by side:
TABLE #3
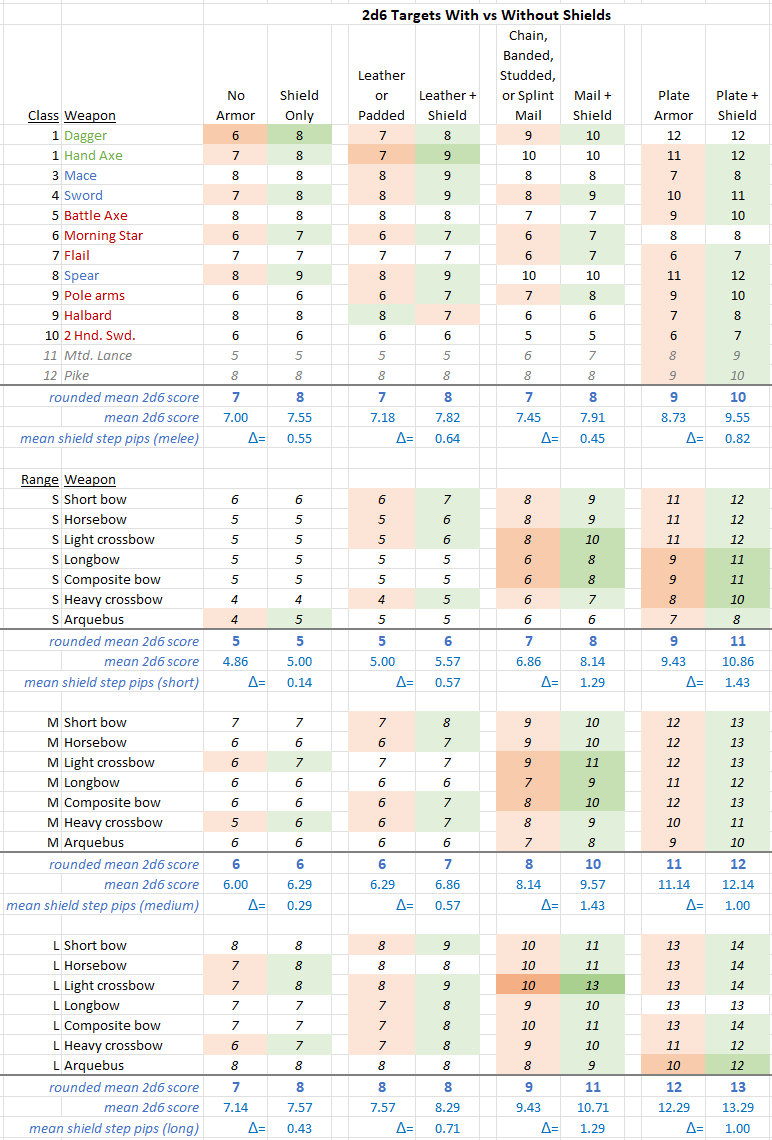
As above, the color in this table indicates which armor in each pair (without and then with shield), offers better protection. Green is better protection, red is worse protection. No color means the protection is the same.
Below each section (in blue) we have the usual mean decimal 2d6 score required to kill versus each armor type without and then with sheild (excluding Mtd. Lance and Pike). Below (indicated by the triangle, delta, symbol) is the difference between each pair of means (armor without and with shield) as a number of 2d6 pips.
Observations:
- Against melee weapons: Shields improve protection in 26 of 44 cases, have no effect in 17 of 44 cases, and decrease protection in 1 case (Leather+shield is WORSE than leather alone vs halberds). Overall, shields improve protection by means of 0.55 to 0.82 pips on 2d6.
- Against missile weapons: Shields have their least effect (0.14 to 0.43 pips of protection) when combined with no armor (offering almost nothing at short range!), and their greatest effect when combined with mail armor armor (1.29 to 1.43 pips of protection).
Shut Yer Hole! Just Gimme the Percentages!
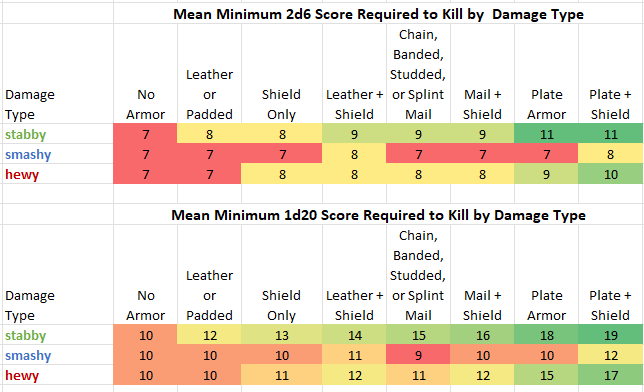
As you doubtless understand already, not all pips in the 2d6 distribution are created equal. So looking at differences in protection as a decimal number of 2d6 pips is not as useful as, say, a bunch of percentages.
Let's convert all those pesky 2d6 target numbers into percentages, and to the nearest 1d20 target numbers while we're at it:
TABLE #4
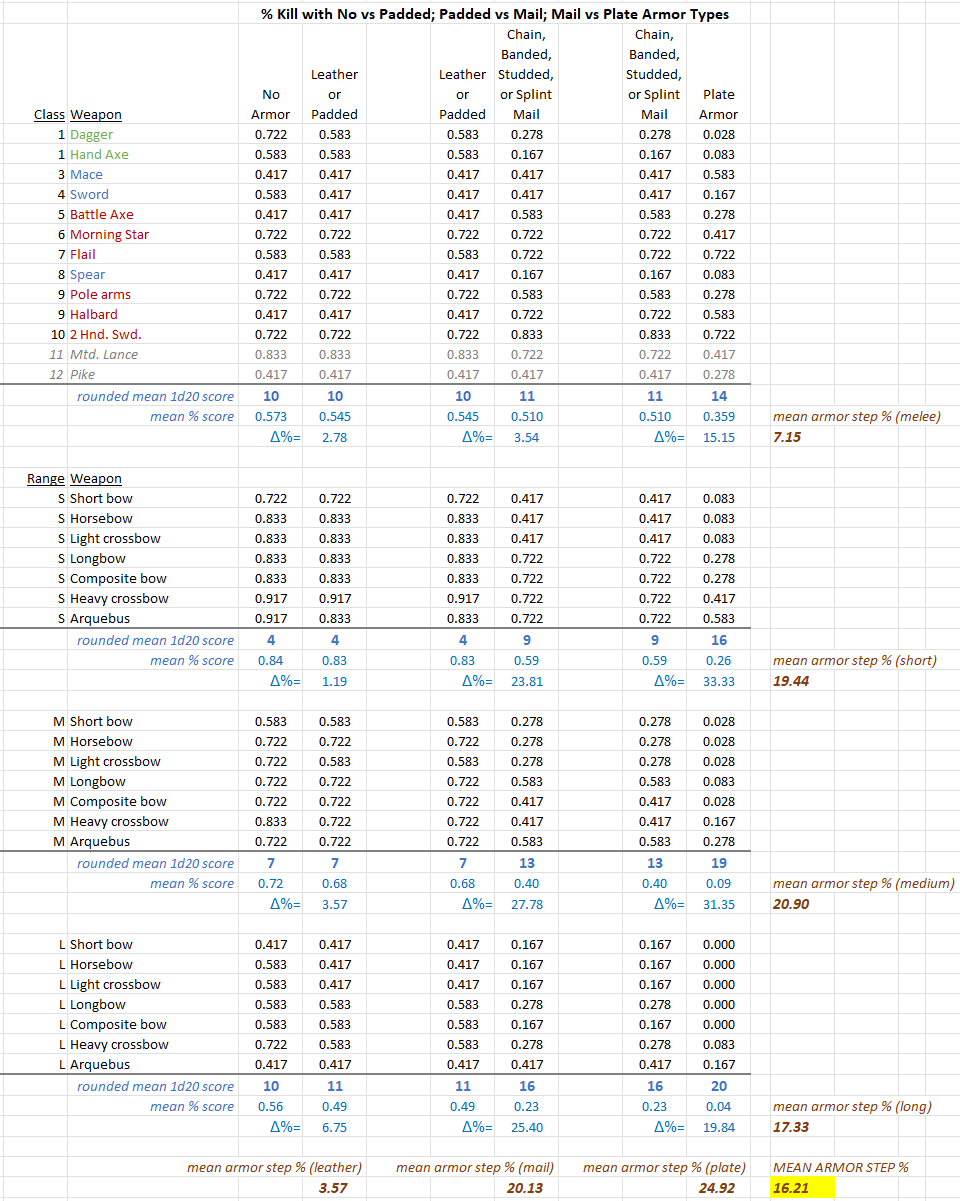
TABLE #5
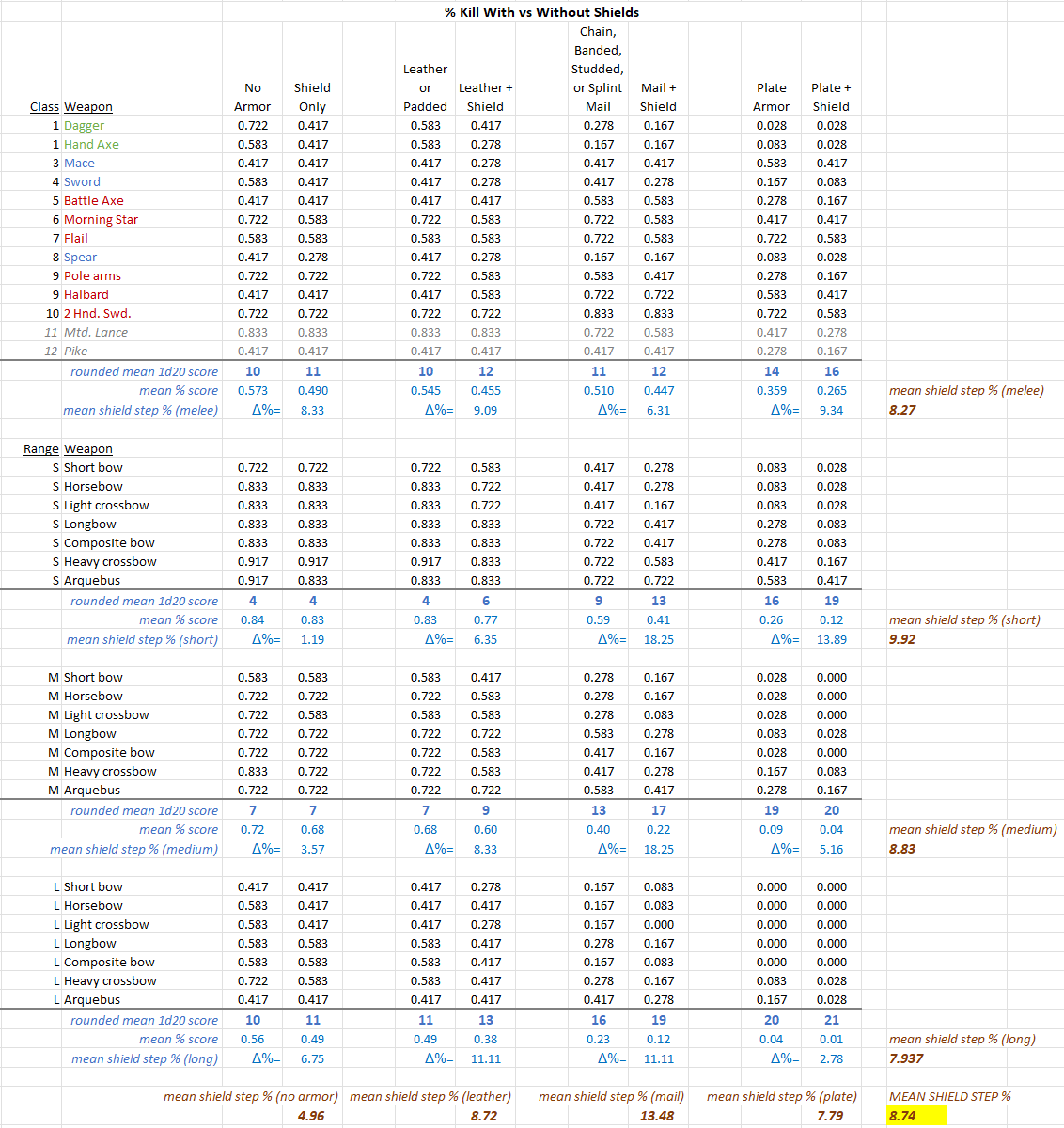
In the body of these two tables, I've converted all the 2d6 scores required to kill to percentages. Then, below each section (in blue) I've calculated:
1. the mean % score required to kill,
2. the rounded mean 1d20 score required to kill, and
3. the % difference between each pair of columns.
All means exclude Mtd. Lance and Pike, as above.
Below and to the side of each table (in brown) is the mean step change across all pairs of means as a %. This tells us about the overall, average rate of progression across the rows and columns, as a %.
Observations:
Melee:
-The rounded mean d20 target scores range from 10 (no armor) to 16 (plate+shield) which is close to D&D's Attack Matrix I (Men Attacking) range, albeit the target numbers are 10, 11, 12 up to mail and shield, only improving to 14 and 16 with plate armor.
-A shield adds a mean of 8.3% protection verus melee weapons, and is consistent across the range.
Missiles:
-At short range (covering most dungeon exploration missile fire) the rounded mean d20 target scores are 4 (no armor, padded) to 9 (mail) to 16 (plate).
-At medium range the rounded mean d20 target scores are 7 (no armor, padded) to 13 (mail) to 19 (plate).
-At long range the rounded mean d20 target scores are 10 (no armor), 11 (padded) to 16 (mail) to 20 (plate).
-The long range d20 target numbers are close to D&D's Attack Matrix I target numbers for 1st level PCs. Medium and short range target numbers are obscenely deadly by D&D standards.
-Shields add a mean of 5%, 8.7%, 13.5%, and 7.8% protection with no armor, padded/leather, mail, and plate armor, respectively.
Final Remarks...
-The M2M authors appear to have had a dim view of padded armor (likely the most common armor of the rules period), and a high opinion of missile fire.
-So, to be a M2M goat, you should maximise use of plate armor and short range missile fire!
What it all means in terms of meeting any set of "historical" and/or gaming expectations (e.g., for use in a medieval wargames campaign such as D&D) is for another post...
In the meanwhile, I hope all that was somewhat entertaining
To that end, I've spent an unjustifiable amount of time/effort in this area, and it has long been on my mind to share some of the outputs here before it all vanishes into oblivion.
Here, I present the Man-to-Man matrix with color (oo!) and percentages (oooh!), and then compare selected columns side-by-side in a hazy attempt to show what's going on. Hopefully, some of this might be useful to anyone interested in the crunch of it...
Man to Man (and Individual Missile Fire) Tables with Color
First up, let's take a look at the minimum (2d6) scores needed to kill (almost*) exactly as they appear in Chainmail, only with COLOR!
* I say "almost" because I have converted the handful of "/ = inability to kill" entries for medium and long range missile fire to 13s and 14s. This nominally means that positive adjustments due to high dexterity and/or magic bows or arrows make it possible to kill in a D&D context where it was impossible in a purely M2M context. Ignore these entries if you prefer.
TABLE #1

The color makes it clearer how effective each weapon type is versus each armor type. The redder a cell is, the more likely a kill. The greener a cell is, the less likely a kill.
Note also:
1. I've colored the melee weapons accorded to Holmes' classification of light (green), regular (blue), and heavy two-handed (red) weapons.
2. Below each weapon section, I've added (in blue) the rounded mean 2d6 score, and decimal 2d6 score required to kill versus each armor type. Mtd. Lance and Pike are excluded from these average calculations as these weapons don't occur in the dungeon exploration context.
Observations:
- The missile weapons show a neat kill probability progression, with both weapon types and armor types listed in least to most effective order. Short range is more effective that medium range, which is more effective than long range.
- The melee weapons do not show the same neat kill probability progression, despite the armor types still being listed in least to most effective order and weapons being listed in size/reach order.
- Considering the mean 2d6 scores required to kill in melee combat, armor other than plate/plate+ shield has small impact on survivorship.
- Considering the mean 2d6 scores required to kill with missile fire; missile fire is even more deadly than melee combat, and especially so for lightly or unarmored targets at short range.
How Effective is my Armor?
If we wanted to see more clearly how effective each ARMOR TYPE is compared to the last, we can simply put the appropriate pairs of columns together, like this:
TABLE #2

The color in this table indicates which armor, in each pair, offers better protection. Green is better protection, red is worse protection. No color indicates that protection is the same.
Below each section (in blue) I've again added the mean decimal 2d6 score required to kill versus each armor type (excluding Mtd. Lance and Pike). Below that, I've added the difference between each pair of means (the triangle, or delta, symbol) as a number of 2d6 pips.
Observations:
- Leather/padded armor is little better than no armor at all (expecting, perhaps, versus missiles at long range).
- Against melee weapons: mail armor (and its variants) is WORSE than leather/padded armor almost as often as it is better. In each case where mail is worse than leather/padded it is also worse than no armor at all!
- Against melee weapons: the improvement offered by plate amor is four-fold as great as the improvements offered by mail over padded/leather, or padded/leather over no armor at all.
- Against missile weapons: the improvement offered by plate amor is again almost double the improvements offered by mail over padded/leather, or padded/leather over no armor at all.
How Effective is my Shield?
Equally, we may wonder what protection SHIELDS offer on the M2M matrix. We can visualise this similarly by comparing the protection of each armor type without and then with shield, side by side:
TABLE #3

As above, the color in this table indicates which armor in each pair (without and then with shield), offers better protection. Green is better protection, red is worse protection. No color means the protection is the same.
Below each section (in blue) we have the usual mean decimal 2d6 score required to kill versus each armor type without and then with sheild (excluding Mtd. Lance and Pike). Below (indicated by the triangle, delta, symbol) is the difference between each pair of means (armor without and with shield) as a number of 2d6 pips.
Observations:
- Against melee weapons: Shields improve protection in 26 of 44 cases, have no effect in 17 of 44 cases, and decrease protection in 1 case (Leather+shield is WORSE than leather alone vs halberds). Overall, shields improve protection by means of 0.55 to 0.82 pips on 2d6.
- Against missile weapons: Shields have their least effect (0.14 to 0.43 pips of protection) when combined with no armor (offering almost nothing at short range!), and their greatest effect when combined with mail armor armor (1.29 to 1.43 pips of protection).
Shut Yer Hole! Just Gimme the Percentages!
As you doubtless understand already, not all pips in the 2d6 distribution are created equal. So looking at differences in protection as a decimal number of 2d6 pips is not as useful as, say, a bunch of percentages.
Let's convert all those pesky 2d6 target numbers into percentages, and to the nearest 1d20 target numbers while we're at it:
TABLE #4

TABLE #5

In the body of these two tables, I've converted all the 2d6 scores required to kill to percentages. Then, below each section (in blue) I've calculated:
1. the mean % score required to kill,
2. the rounded mean 1d20 score required to kill, and
3. the % difference between each pair of columns.
All means exclude Mtd. Lance and Pike, as above.
Below and to the side of each table (in brown) is the mean step change across all pairs of means as a %. This tells us about the overall, average rate of progression across the rows and columns, as a %.
Observations:
Melee:
-The rounded mean d20 target scores range from 10 (no armor) to 16 (plate+shield) which is close to D&D's Attack Matrix I (Men Attacking) range, albeit the target numbers are 10, 11, 12 up to mail and shield, only improving to 14 and 16 with plate armor.
-A shield adds a mean of 8.3% protection verus melee weapons, and is consistent across the range.
Missiles:
-At short range (covering most dungeon exploration missile fire) the rounded mean d20 target scores are 4 (no armor, padded) to 9 (mail) to 16 (plate).
-At medium range the rounded mean d20 target scores are 7 (no armor, padded) to 13 (mail) to 19 (plate).
-At long range the rounded mean d20 target scores are 10 (no armor), 11 (padded) to 16 (mail) to 20 (plate).
-The long range d20 target numbers are close to D&D's Attack Matrix I target numbers for 1st level PCs. Medium and short range target numbers are obscenely deadly by D&D standards.
-Shields add a mean of 5%, 8.7%, 13.5%, and 7.8% protection with no armor, padded/leather, mail, and plate armor, respectively.
Final Remarks...
-The M2M authors appear to have had a dim view of padded armor (likely the most common armor of the rules period), and a high opinion of missile fire.
-So, to be a M2M goat, you should maximise use of plate armor and short range missile fire!
What it all means in terms of meeting any set of "historical" and/or gaming expectations (e.g., for use in a medieval wargames campaign such as D&D) is for another post...
In the meanwhile, I hope all that was somewhat entertaining